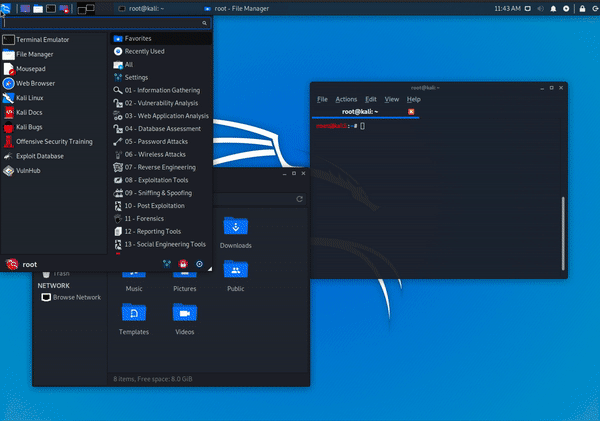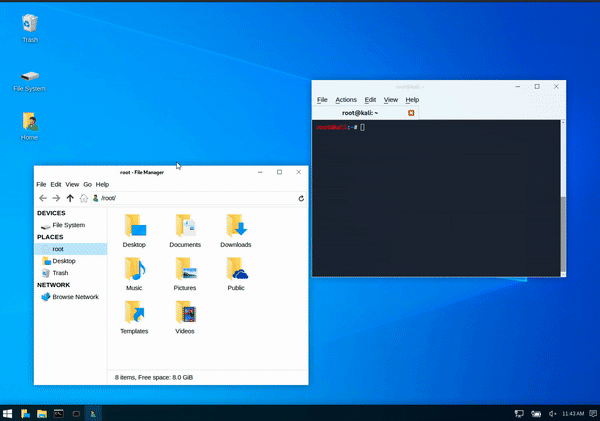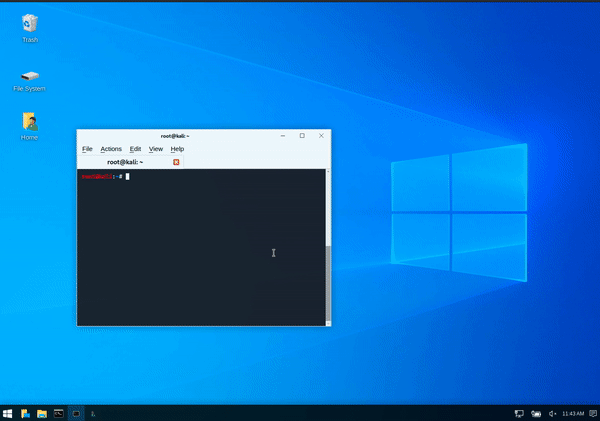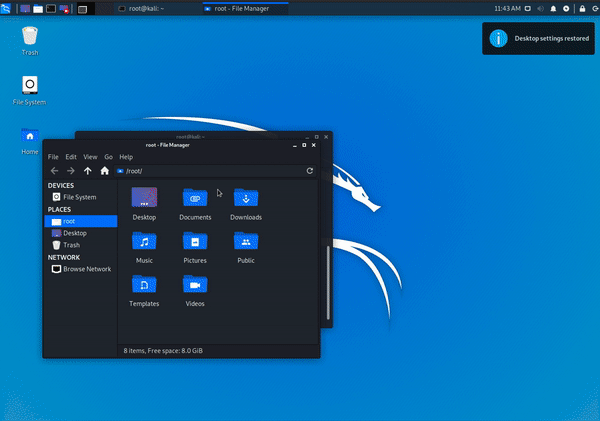
We're our own focus group' – Ning Wang on security certification, training, and keeping Kali Linux on top | The Daily Swig

FinSpy (aka FinFisher) spyware for Windows, macOS, Linux, Android, and iOS | Kaspersky official blog

Hands-On Penetration Testing with Kali NetHunter: Spy on and protect vulnerable ecosystems using the power of Kali Linux for pentesting on the go 1, Singh, Glen D., Oriyano, Sean-Philip, eBook - Amazon.com





![Find Information from a Phone Number Using OSINT Tools [Tutorial] - YouTube Find Information from a Phone Number Using OSINT Tools [Tutorial] - YouTube](https://i.ytimg.com/vi/WW6myutKBYk/maxresdefault.jpg)